
Why Was Prefetch Created in Windows?
When Microsoft introduced Prefetching with Windows XP, it wasn't designed for cybersecurity or digital forensics—it was all about performance optimization. At its core, Prefetch is a subsystem of the Windows Memory Manager that helps speed up the boot process and the launching of frequently used applications. From a system-efficiency perspective, Prefetch was a smart way to reduce application load times. But from a digital-forensics standpoint, Microsoft unintentionally created a timeline goldmine.
What Is a Prefetch File?
A Prefetch file is a binary file created by the Windows operating system when an executable is run. Its primary job is to help Windows optimize application loading by remembering what resources (such as files and DLLs) were accessed during that app’s launch. The cache manager monitors all files and directories referenced for each application and records them into the corresponding .pf file. On Windows 8 and above, there can be up to 1,024 files waiting for you in the Prefetch folder.
Forensic Value of Prefetch Files
Each prefetch filename combines the executable name (CHROME) and a hash of its path (e.g., CHROME-94AA1033.pf). Prefetch files flag application execution and embed metadata such as run count, original execution path, and last execution time.
📌 Keep an eye out for multiple prefetch files with the same executable name. This usually means the same-named executable was run from different locations. If you see severalcmd.exeprefetch files, it could point to a roguecmd.exeoutside the standardC:\\Windows\\System32folder—potentially a valuable finding!
Prefetch Analysis: First & Last Execution Times
1. First Executed: The creation date indicates the first execution (~10 s window).
2. Last Executed: The modification date captures the most recent execution (~10 s window).
If an app hasn’t run recently, its prefetch file may age out and be deleted. Upon the next run, Windows creates a new .pf file with a fresh creation time. Prefetch metadata isn’t written until roughly 10 s after execution starts.
📌 A .pf file doesn’t guarantee successful execution—broken programs can still generate prefetch entries.
Prefetch Analysis with PECmd.exe
PECmd.exe (by Eric Zimmerman) parses Windows Prefetch files, extracting volume info, file references, run counts, and execution timestamps.
C:\> PECmd.exe -f CHROME-94AA1033.pf
C:\> PECmd.exe -d "D:\[USER]\Windows\Prefetch" --csv "G:\cases" --csvf result.csv
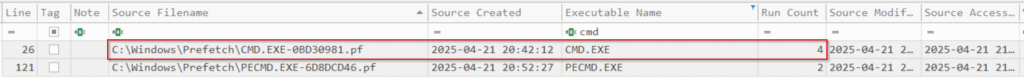
Parsing a directory produces a detailed CSV of run metadata plus a timeline view. Opening results.csv in Timeline Explorer lets us filter, e.g., all cmd.exe executions (four in this sample).
Conclusion
Prefetch analysis is invaluable in digital forensics, revealing execution timelines and evidence of suspicious activity. Combine Prefetch insights with other artefacts to build a comprehensive incident picture.